LINUX
CYBERLAW
VIRTUALIZATION
Bugtraq
Packetstorm
FD
GrokLaw
RSS Feed
Netsec, comsec, infosec and IA news, research and trends
12.30.2008
MD5 considered harmful today: Creating a rogue CA certificate by Alexander Sotirov, Marc Stevens, Jacob Appelbaum, Arjen Lenstra, David Molnar, Dag Arne Osvik, Benne de Weger
12.29.2008
Attacking Critical Internet Infrastructure - Alex Sotirov and Jacob Appelbaum's live presentation will be available online via streaming video at 3:15pm (9:15am EST on Tuesday, December 30th.
It will be interesting to see what Alex Sotirov and Jacob Appelbaum present in their CCC talk "Making the theoretical possible: Attacking a critical piece of Internet infrastructure."
12.20.2008
Pen testing web servers - A good pen-test narrative from Dave at the Daily Dave
12.19.2008
Volatility Blog - The Volatility Framework: Volatile memory artifact extraction utility framework
MANDIANT Memoryze is free memory forensic software that helps incident responders find evil in live memory. Memoryze can acquire and/or analyze memory images, and on live systems can include the paging file in its analysis.
12.17.2008
Random number generator - The randomness comes from atmospheric noise, which for many purposes is better than the pseudo-random number algorithms typically used in computer programs.
Robert Seacord on the CERT C Secure Coding Standard
Microsoft: Emergency Patch for IE 0-day Coming Today
12.16.2008
Pay attention to cyberlaw from Mich
12.15.2008
Serious flaw in Internet Explorer not fixed yet. Specifically, its continued use
12.12.2008
What we suddenly don't know about the new IE exploit from Leyla
12.11.2008
Ruh-Roh - Checkpoint Sources plus SPLAT Remote Root Exploit
12.08.2008
with proper credit to http://www.dilbert.com
12.04.2008
70% of small/medium enterprises will enter 2009 with networks at risk of security breach
More info on the San Francisco security fiasco earlier this year
Australia plans mandatory nation-wide internet filtering
11.21.2008
Internet Law Update: Court Sharply Limits Patentability of Business Methods Patents: In re Bilski, Case No. 2007-1130
I heard of the issue regarding USB devices spreading viruses a while back and feel compelled to say that this is not a technical problem, it is a human problem... a stupid human problem. In the past, some have treated my suggestion of epoxy as an permanent fix for this issue as apostasy. "What???? Ban USB devices??? That's crazy!"
NetWitness Investigator (Free)
11.20.2008
Here is why USB drives have banned by the military until further notice.
http://blog.wired.com/defense/info_war/index.html
11.17.2008
McColo takedown nets massive drop in spam
11.13.2008
Nicolas Waisman: Apology of 0days (from H2HC in Sao Paolo)- Immunity's 0day numbers: Average 0day lifetime: 348 days, Shortest life: 99 days, Longest life: 1080 (3 years).
11.12.2008
Elcomsoft researchers achieve 100-fold increase in WPA2 cracking speed from Brett
11.11.2008
US Navy hacker avoids Romanian jail.
CTO of the United States? - Read the technology related policy proposals here
Spring 2009 - Priority Registration Now Open (Regular registration begins Nov 17th)
ITN 260 Network Security Basics – Face-to-Face Course #25429 Section #N01C Wednesdays 6-9:30pm - Online Course#25435 Section# O02C - This course lays the foundation for further study in the network security program. Content domains include cryptography, communications security, infrastructure security, operating system security, wireless security, intrusion detection, malicious software, common attacks, and countermeasures.
ITN 261 Network Attacks, Computer Crime and Hacking Tuesdays 6-9:30pm Course #39887 Section N01C - In ITN 261, students learn about security testing and vulnerability assessment strategies. From port scan to buffer overflow, hands-on labs teach students effective computer/network attack/defense techniques.
ITN 275 Incident Response and Computer Forensics – Course # 25455 Section # N01C - Thursdays 6:00 pm – 9:30pm. In this intense hands-on course, students investigate live scenarios involving computer intrusion events, conspiracy, and espionage.
Spring 2009 Linux / Unix Courses
ITN 171 Unix I - Online 4 credits - Course #39883 Section O01C Provides an introduction to UNIX and UNIX-like operating systems. Teaches login procedures, file creation, UNIX file structure, input/output control, the UNIX shells, and shell scripting.
ITN 170 Linux System Administration - Course #25431 Section N01C Monday Evenings 6:00pm – 9:30pm 4Cr Focuses on the installation, configuration and administration of the Linux operating system. Emphasis is placed upon use of Linux as a network client and workstation. Leads to Red Hat Certified Technician (RHCT) Certification. Prerequisite: ITN 171
ITN 270 Advanced Linux Network Administration – Course #25437 Section N01C – Wednesday Evenings 6:00pm – 9:30pm 4Cr. Focuses on the configuration and administration of the Linux operating system as a network server. Emphasis is placed upon the configuration of common network services and security. Leads to Red Hat Certified Engineer Certification. Prerequisite: ITN170
11.07.2008
Battered, but not broken: understanding the WPA crack
Computers at the headquarters of the Barack Obama and John McCain campaigns were hacked during the campaign by a foreign entity looking for future policy information
11.06.2008
Aircrack-NG Adds WPA Cracking Support previously only available in KisMAC
10.30.2008
Goodbye, electronic voting. Farewell, fancy touch screen. Maryland and Virginia are going old school after Tuesday's election.
10.29.2008
Windows RPC hole being exploited in the wild
10.28.2008
District Court Holds that Running Hash Values on Computer Is A Search - United States v. Crist, 2008 WL 4682806 (M.D.Pa. October 22 2008) (Kane, C.J.)
10.24.2008
The Atlas of Cyberspace, by Martin Dodge and Rob Kitchin is now available for free online under a Creative Commons license.
10.20.2008
Compromising the Electronic Emanations of Wired Keyboards by Martin Vuagnoux and Sylvain Pasini
10.17.2008
Microsoft Windows Internet Printing Protocol service integer overflow being exploited in the wild.
10.15.2008
Rafal Wojtczuk - "Adventures with a certain Xen vulnerability (in the PVFB backend)"
10.14.2008
World Bank (Allegedly) Hacked
[Dailydave] The Static Analysis Market and You
10.13.2008
Uninformed Journal Number 10 Released
Russian researchers achieve 100-fold increase in WPA2 cracking speed
10.10.2008
Token Kidnapping Windows 2003 PoC exploit
Quick! Call the news!
10.08.2008
EU scientists launch new, 'unbreakable' encryption system from Leyla
10.05.2008
Explaining the “New” TCP Resource Exhaustion Denial of Service (DoS) Attack
10.04.2008
Why Risk Management Doesn't Work from Tracy
9.29.2008
Last Chance: Tell Bush to veto the RIAA/MPAA Enforcement Bill
From revision3.com, here is a program now available on your Tivo called HAK5 which covers network admin, black hat, white hat, and gaming. Recent episodes include topics like "hacking a wireless network with a pineapple," "analysis of a virus infection in windows," and "monitoring your network assets with spiceworks." This appears to be a locally filmed (i.e. Williamsburg) show with guests from Hampton Roads. For those of you not familiar with Revision 3, I highly recommend you check out some of the growing number of tech shows now available through this organization including Systm, Tekzilla, and Diggnation
9.28.2008
Paul Craig discussed a new way of owning a system by using his newly released 'Moth Trojan' today at Kiwicon in New Zealand. Paul also took owning a kiosk to a new level with hi
9.26.2008
Dealing with UI redress vulnerabilities inherent to the current web - by Michal Zalewski
9.23.2008
Download Helix 3.0 - MD5=93a285bfa8ab93d664d508e5b12446d3
9.22.2008
Helix 2008R1 released (Ubuntu) changelog
Off topic: Security for your home/office using WowWee's WiFi-enabled Rovio. Shipping this month. Not sure what type of wireless encryption this may use if any.
9.21.2008
http://www.neopwn.com/ new pentesting mobile phone.
9.19.2008
NIST: Profile for IPv6 in the U.S. Government from Chainman
9.17.2008
Palin's Email Compromised and Posted to Wikileaks
9.16.2008
Student faces charges for hack-and-tell from Chainman
Berners-Lee of W3C says websites should have a trustworthiness label.
9.13.2008
Air Force Cyber Command Could Return, With Nukes
9.11.2008
San Francisco hunts for mystery device on city network from Chainman
9.10.2008
Online Posse Assembles, to Unmask Russia's Hackers from Ryan
Defeating Encrypted and Deniable File Systems: TrueCrypt v5.1a and the Case of the Tattling OS and Applications - from Brett
Why All the Data Breaches? Businesses Just Don’t Care from Chainman
9.08.2008
One Bad Apple from Luis
Pentagon debates development of offensive cyberspace capabilities - from Chainman
More on AF Cyber Hiatus
9.06.2008
The CERT Virtual Training Environment (VTE) - A revolutionary resource for information assurance, incident response and computer forensic training, with over 500 hours of material available. VTE blends the best of classroom instruction and self-paced online training, delivering training courses, anytime access to answers, and hands-on training labs all through a standard Web browser. From Dale.
9.04.2008
IPv6 = Metavulnerability? - Yet another Remote IPv6 (ICMPv6) Flaw in FreeBSD
9.03.2008
Immunity Debug Register (DR) Linux Rootkit (loads via insmod so monolithic kernels with the module loader omitted should not be vulnerable)
Google unveils open-source browser - Chrome - Proof-of-Concept DOS Exploit Released
8.29.2008
DNSSEC Mandated for .GOV by Jan 2009 - The memo states that "DNSSEC provides cryptographic protections to DNS communication exchanges, thereby removing threats of DNS-based attacks..." Wow. Where can one buy a pair of those rose-colored glasses?
8.27.2008
Computer viruses in space. Not to be confused with pigs in space
Revealed: The Internet's Biggest Security Hole
8.21.2008
Open Source Spear-Phishing Assessment Tool to Be Released Next Month at the OWASP Conference from Chainman
8.20.2008
Judge nixes gag order against MIT students - What a sham the entire case has been! The case was never going to stick anyway.
8.19.2008
Spam from the botnet, for the botnet from Chainman
8.16.2008
NIST revises guidance for assigning FISMA security categories
DefCon CTF 2008 Wrap-Up - There's been a bit of whinging on the DailyDave about the tournament.
8.14.2008
Computer Scientists Ask Court to Reconsider Gag Order in DefCon Case
8.13.2008
KARMA + Metasploit 3 == Karmetasploit
Georgia: Before the Gunfire, Cyberattacks
8.12.2008
Ru-Roh - Exploit successfully poisons latest BIND with fully randomized ports
8.11.2008
Dan Kaminski's DNS Presentation from Defcon
8.09.2008
Hardware Trojans - Professor Fouad Kiamilev and Ryan Hoover of University of Delaware produced some interesting hardware Trojan demos using optical, radio, and thermal sources to transmit AES keys from a compromised system.
The 11th U.S. District Court has issued an injunction against the presentation "Anatomy of a Subway Attack" by Russel Ryan, Zack Anderson, and Allesandro Chiesa which was scheduled for tomorrow at 1pm. According to the EFF, the plaintiffs will not likely prevail on their established legal rationale which was the CFAA prohibition against knowingly causing "the transmission of a program, information, code, or command, and as a result of such conduct, intentionally" causing "damage without authorization, to a protected computer." If this stands it could have a chilling effect on free speech.
8.07.2008
Defcon 16 Presentations
8.06.2008
Black Hat USA 2008 Presentations
Professor Ian Angell from the London School of Economics has been my favorite presenter thus far [PPT]. He's giving the keynote at Defcon and I plan on seeing that as well. He offered some rigorous critiques of IS, AI, misapplication of statistics, and the general fallibility of mankind. Big picture topics that served to broaden the scope of the security discussion society really needs to have one day (but will never happen).
There are so many good talks that it is difficult to choose. Some favorites covered hardware rootkits, attacking virtualization, and writing shellcode for Cisco devices. The presenters of the Cisco shellcode talk picked up where Mike Lynn left off in 2005. Cisco's security practices would likely never be tolerated in a commercial OS (of course, consumers put up with a lot due to ignorance or laziness) - no virtual memory implementation, no process separation, everything runs in a single flat address space with full system privs. As a result, shell code is easy to write and exploitation even easier as every process has full rights to all heap data.
8.04.2008
California Secretary of State Debra Bowen supports paper ballots - Top to bottom review of e-Voting systems included code review and pen-tests (led by Matt Bishop) - 0wn the Vote! The Diebold (GEMS Server and Accuvote) system runs on an unpatched Windows 2000 Server!
DNA identification may not be reliable
Blue Cross and Blue Shield exposes 202,000 customers
8.01.2008
Large Hadron Collider nearly ready
Papers from the 2nd Annual USENIX Workshop On Offensive Technology
7.31.2008
Kansas Senator (Brownback) Blasts Chinese Government For Ordering Internet Surveillance - Brownback must be concerned about China competing with the US when it comes to spying on it's own citizens.
Paper Catalog + Computer Database = Patent? Um, No.
Senators Announce New Intellectual Property Enforcement Bill - Why??? Enforcement of civil law is traditionally (and best) left to the harmed party or parties. Is DOJ prepared to force the FBI to start investigating copyright infringement (again) despite the fact such frivolous issues would steal resources away from much more pressing matters? I do not think that anyone could possibly want this bill to pass other than special interests in Hollywood.
7.29.2008
WEIS 2008: Do data-breach-disclosure laws reduce identity theft?
7.28.2008
Air Force Cyber Command: Building the Infrastructure for High-Tech War Crimes - I am unashamedly liberal (in the Thomas Paine/Adam Smith way, not the nanny-state sort of way) but even I have to say that the author must be off his meds. Mr. Burghardt apparently thinks that it is better to engage an opponent with bombs and bullets than bits and bytes. If information warfare and operations (IW/IO) means fewer casualties of war, I am all for it. Numerous nations are already involved in non-stop, slow simmering information-based adversarialism. To not develop capabilities in this space would be to surrender the battleground. That said, it is important to ensure that the actions of the AFCC comply with the Constitution as well as the laws of the US, the States, and any applicable international agreements. To that end, I fully support the intent of the author. Democracy is noisy and loud and it means having to put up with all sorts of crackpot theories from both the left and the right.
DE-ICE PenTest LiveCD disks "provide a safe and secure way to learn and practice Penetration Test skills" from Matt
7.24.2008
Webinar: Dan Kaminsky's DNS Discovery: The Massive, Multi-Vendor Issue and the Massive, Multi-Vendor Fix
7.23.2008
DNS Cache Poisoning POC Released
The Story Behind San Francisco's Rogue Network Admin - from Andrew
NAT being added to IPv6
7.22.2008
Kaminsky's DNS Issue Accidentally Leaked?
Julie Amero Case Drags On
7.18.2008
HSM - Home Security Methodology Vacation Guide
7.17.2008
Researcher to demonstrate attack code for Intel chips
U.S. Fears Threat of Cyberspying at Olympics - While the threat is real (there will almost certainly be mass compromises during the Olympics), it is unfortunately an issue in both China and the US
BlackBerry Warns About PDF Distiller Flaw
The DEFCON Shoot Returns with Full-Auto, Class III Firearms
7.16.2008
Kon-Boot allows one to change the Linux kernel on the fly (while booting)
7.15.2008
DHS Privacy Office - Privacy Workshops - Implementing Privacy Protections in Government Data Mining
Are these people out of their minds? - Why stop at the airport gate?
And you thought air travel could not get any worse. An official with the Department of Homeland Security says the U.S. should consider having airline passengers wear electronic bracelets that could track their movements, hold personal information and be triggered like a Taser to stun them into immobility.
UK to Implement Biometric ID by 2009
An Astonishing Collaboration - More on the BIND Bug from Dan Kaminski: "DJBwas right. All those years ago, Dan J. Bernstein was right: Source Port Randomization should be standard on every name server in production use.
There is a fantastic quote that guides a lot of the work I do: Luck is the residue of design. Dan Bernstein is a notably lucky programmer, and that’s no accident. The professor lives and breathes systems engineering in a way that my hackish code aspires to one day experience. DJB got “lucky” here — he ended up defending himself against an attack he almost certainly never encountered.
Such is the mark of excellent design. Excellent design protects you against things you don’t have any information about. And so we are deploying this excellent design to provide no information."
7.13.2008
TrackMeNot - a lightweight browser extension that helps protect web searchers from surveillance and data-profiling by search engines. From Tarik
7.11.2008
Dutch chipmaker sues to silence security researchers - from Anthony
7.10.2008
Insomnia Security - Whitepaper Collection
The 2nd Annual Pwnie Awards - An annual awards ceremony celebrating and making fun of the achivements and failures of security researchers and the wider security community - Nominations close July 14th.
FBI Headquarters Not Cleared for Classified Intelligence - from Anthony
7.09.2008
Snuggly The Security Bear Presents "Constitutional Compromise"
Multiple DNS implementations vulnerable to cache poisoning
7.07.2008
Art and Practice of Deception
Quick access to hidden **** browser passwords - Che'
7.04.2008
Thieves steal millions from Citibank customers via 7-11 ATMs
7.02.2008
Inside NSA Red Team
VMware Infrastructure Earns Common Criteria EAL4+ Certification - from Chainman
I know it's anathma to post stories from Slashdot, but PC Repair in Texas now requires a PI license?
7.01.2008
OpenBSD ICMPv6 Exploit from LMH
6.30.2008
DPE - Default Password Enumeration
6.28.2008
Malicious Code 2008
6.27.2008
Blizzard Implements Token Based Access Control System for World of Warcraft from Matt
6.25.2008
BitBlaze - Binary Analysis for COTS Protection and Malicious Code Defense
Automatic Patch-Based Exploit Generation is Possible: Techniques and Implications
IATAC Newsletter
6.24.2008
New revision: NIST 800-61 Computer Security Incident Handling Guide
6.18.2008
The Extended HTML Form attack revisited
New DNSChanger Trojan variant targets routers - from Dave
Tree Approach to Vulnerability Classification
6.17.2008
Verizon 2008 Data Breach Investigations Report
6.15.2008
Economics, Psychology, and Sociology of Security
Tracking the Trackers - Investigating P2P Copyright Enforcement
The ID Divide - Addressing the Challenges of Identification and Authentication in American Society
Electronic Crime Scene Investigation: A Guide for First Responders, Second Edition
Built-in Windows commands to determine if a system has been hacked
Shops track customers via mobile phone
Compromising Reflections – or – How to Read LCD Monitors Around the Corner
6.14.2008
The NSF Grand Challenge: Unhackable Servers
6.13.2008
China denies hacking congressional computers - Che'
6.12.2008
N.Y. attorney general forces ISPs to curb Usenet access
6.11.2008
Proof of Concept “carpet bombing” exploit released in the wild - from Anthony
FreeType2 Heap Overflows in Parsing PFB and TTF Font Files Lets Remote Users Execute Arbitrary Code from Che
6.10.2008
Credit, debit cards move to chip technology - from Cheryl
6.09.2008
Military supercomputer sets record
How safe is instant messaging? A security and privacy survey - from Anthony
6.05.2008
Scientists Study Human Movements Through Secret Cell Phone Tracking. "The cell phone users who were the unwitting subjects of the study were reportedly based in an undisclosed country other than the United States, and they were tracked through the participation of an unnamed carrier. Because they were unaware that they were being tracked, however, the new research has generated a wave of discussion about the privacy implications."
Internet Scheme Used to Steal Micro-Deposits from Che
6.04.2008
Warning: Dangerous Web surfing ahead - from Luis
Fortunately, Micah Sherr maintains a link to the EVEREST Report
Full Disclosure and why Vendors Hate it
E-Voting Flaw Gives Election Victory to Wrong Candidate
Borked elections due to E-Voting flaws/errors have occurred before in Ohio at least Twice! Two brothers control nearly 100% of the E-Voting hardware used in the US. Bob Urosevich controls Diebold while his brother Todd controls ES&S [more]. In a 2003 fund-raising e-mail, the then-CEO of Diebold, Walden O'Dell, promised to deliver Ohio's electoral votes to a given candidate in 2004. If you have not read the report issued by the Ohio Secretary of State Jennifer Brunner "Evaluation & Validation of Election-Related Equipment, Standards & Testing" AKA EVEREST , you should... it enumerated over 300 known issues with the current generation of E-Voting hardware. Despite the report, the Ohio Election Commissioners voted to do nothing about it.
The next election may have already been decided.
Bank loses tapes with data on 4.5M clients - Connecticut AG blasts BNY Mellon for failing to notify victims for three months
Beware of Error Messages At Bank Sites
6.03.2008
Core Security: The Academy
6.02.2008
Phoenix Mars Lander Website Hacked
6.01.2008
Privacy Impact Assessment for EINSTEIN 2
Privacy and the 2008 Olympic Summer Games - RFID tagged tickets to track passport details, address, and other personal data.
China's All-Seeing Eye - With the help of U.S. defense contractors, China is building the prototype for a high-tech police state. It is ready for export.
A Low-cost Attack on a Microsoft CAPTCHA
Motorola RAZR JPG Processing Stack Overflow Vulnerability
E-voting banned by Dutch government
5.31.2008
The Shmoocon 2008 videos are out! w00t!
5.30.2008
The Last Hope - July 18-20
US probes whether laptop copied on China trip
5.29.2008
Comcast home page hacked - from Anthony
Risk report: Three years of Red Hat Enterprise Linux 4
Enterprise Linux 5.1 to 5.2 risk report
5.28.2008
Six hours to hack the FBI (and other pen-testing adventures)
5.27.2008
NVbit : Accessing Bitlocker volumes from linux
Bordering on insanity - Why you probably shouldn't bring any sensitive data across U.S. borders
Google Adds to Search Engine Security from Mary
5.23.2008
Certifiable Linux Integration Platform defines a specific configuration of Security Enhanced Linux (SELinux) designed to provide the foundation for hosting secure applications.
Inside an FBI Computer Forensics Lab
5.22.2008
EFF: Release the Orphan Works!
5.21.2008
Permanent Denial-of-Service Attack Sabotages Hardware - from Anthony
5.20.2008
Core Security IOS Rootkit
5.16.2008
Uhoh!
Looks like the NIC vendors are going to have to dance with the rest of them....
5.15.2008
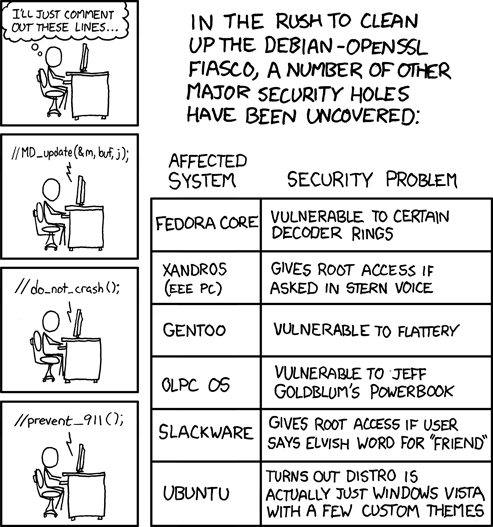
More on the Debian OpenSSL Bug
Thinking Beyond the Ivory Towers by Dave Aitel
DSA-1571-1 openssl -- predictable random number generator
Google Oops - Create a Google Apps spreadsheet and hide some of the data fields. Highlight the whole spreadsheet and copy (ctrl+c). Open a spreadsheet app like Excel and paste. Oops. That data was not quite so hidden after all!
5.09.2008
FBI Fears Chinese Hackers and/or Government Agents Have Back Door Into US Government & Military Computer Networks - NY Times Article
I have had a number of opportunities come up this week in both IT and IA:
#1) General IT - When presented a project the candidate does not need to be an expert at the start. However, with some research and a little trial and error should be able to become an expert. A willingness to learn is key. Active Directory, TPC/IP, Networking; Routers, Firewalls, design, Windows XP, MACs, Some Linux exposure - 30k to 40k.
#2 General helpdesk/desktop support with AD/server 2003 duties. Occasional Cisco work under supervision. Little to no management duties. $40-$50k - a little more w/ more experience. $4500 tuition support per year!
#3 Local Blue Team positions (cooperative security assessment, evaluation, testing, and remediation)- 50-70% travel. Salary commensurate with experience.
#4 Similar to #3 but for someone willing to move to Monterrey, CA. Salary commensurate with experience.
If you are or someone you know is interested, qualified, and trustworthy, please send me a resume!
5.07.2008
FBI Withdraws Unconstitutional National Security Letter After ACLU and EFF Challenge
5.05.2008
California court posting SSNs and other personal data, privacy advocates charge
5.03.2008
Is Red Hat Owned or Simply Offline?
4.30.2008
Microsoft COFEE - Just what we need.... more untrained amateurs gathering digital evidence.
4.29.2008
How German Spies Eavesdropped on an Afghan Ministry
4.28.2008
RIAA on the Defensive - from Keith
4.27.2008
A Gift from the Islamic Faithful Network - Mujahedeen Secrets 2 Program
4.25.2008
Defcon Contests - Race to Zero
4.24.2008
Denial of Service via Algorithmic Complexity Attacks
Crooks Rig ATM with Eee PC to Steal Credit Card Info from Steve
4.23.2008
Border Agents Can Search Laptops Without Cause, Court Rules.
Thinkgeek's $1,589.99 Keyboard
Lending Tree Compromised 2006~2008 - from Luis
4.22.2008
NJ court blocks IP disclosure without a grand jury subpoena
4.21.2008
Military Fellows Roundtable: Air Force Cyberspace Command: Protecting Against an Electronic Pearl Harbor
Token Kidnapping by Cesar Cerrudo
The 10,000 web sites infection mystery solved
4.18.2008
One reason that security is so difficult to implement is because the end user is typically the weakest link. Although not network security related, this article does show that people "just don't get it"
Ground Zero Blueprints Found in Trash
GSM Cracking: Coming Soon to a Computer Near You via a Web Service
4.15.2008
1st ACM Workshop on Virtual Machine Security (VMSec) - Call for Papers
4.12.2008
Application-Specific Attacks: Leveraging the ActionScript Virtual Machine - Scrapped from the Dailydave - If you do not get it, you should
Security Concepts eBook
4.11.2008
ORNL: Adaptable, Intelligent Malfeasance Detection (AIMD) - "Indifference Detection"?!?
E-Voting Versus Slot Machines - Which is more secure?
4.10.2008
Windows Vista Source Code from Chainman
4.09.2008
Contribute to the Fund to End Software Patents - Software patents undermine "the progress of science and the useful arts."
4.08.2008
Dan Kaminski to Demonstrate How a Web Page Can Take Over a Router at the RSA Conference
4.02.2008
Sguil Project Acquired by Cisco - Announces Plans to Start Randomly Dropping Packets
4.01.2008
TCP/IP security vulnerability disclosed
RFC 2844: The Transmission of IP Datagrams over the Semaphore Flag Signaling System (SFSS)
Gmail introduces time travel service
ZapCam - YouTube Tazer
3.30.2008
From the CarolinaCon EULA - "the plural of anecdote is not data"
3.29.2008
Vista, MacBook Out--Only Linux Left in Hacking Contest - from Clyde
3.26.2008
International Journal of Bayesian Analysis
Software Forensics: Extending Authorship Analysis Techniques to Computer Programs
3.24.2008
Microsoft warns of targeted Word attack
CanSecWest PWN2OWN 2008
3.21.2008
FIPS 140-2 Certified Thumb Drives
Hannaford hit by class-action lawsuits in wake of data-breach disclosure
3.20.2008
[Off Topic] Support Tibet - Boycott the Beijing Olympics
3.19.2008
The A5 (GSM) Cracking Project
[Video] CCC Camp07 GSM Software Project and A5 Cracking Talk
[Paper] TULP2G – An Open Source Forensic Software Framework for Acquiring and Decoding Data Stored in Electronic Devices
[Tool] TULP2G - forensic framework for extracting and decoding data
Paraben - Cell/PDA Forensic Hardware and Software
How Do You Intercept a Text Message?
Arrogance or Efficiency? A Discussion of the Microsoft Office Fluent User Interface
3.17.2008
Trendmicr0wn3d?
3.16.2008
All Usenix conference procedings made public!
3.14.2008
Some viruses come preinstalled (so you wont have to install them yourself!)
GW: This is called "pre0wned" hardware
3.13.2008
First Look: KNOPPIX 5.3.0 - At CeBIT 2008!
Downloaded Knoppix 5.3 here
3.12.2008
A Heart Device Is Found Vulnerable to Hacker Attacks
A report from the Medical Device Security Center
SPAM - Felony conviction upheld - from Clyde
NPS Scholarship Program - "Free" Master's Degree!
3.07.2008
Call for Papers First ACM Workshop on AI Security
3.06.2008
Creating bootable USB drives for capturing the contents of memory
3.04.2008
Major banks, telecos top identity-theft chart
Hack into a Windows PC - no password needed/Physical Access Attacks with Firewire (PDF)
Vista volume activation cracked
Coming to a watering hole near you: OLPC's mesh networking - from Bill
3.03.2008
The CERT Virtual Training Environment (VTE) - A free resource for information assurance, incident response and computer forensic training - from Chainman
OSSTMM V3.0 Introduction Video - from Chainman
Group Demonstrates Security Hole in World's Most Popular Smartcard - Additional details available via Karsten Nohl's UVA Web Page - from Jennifer
2.28.2008
Position Open for SCADA Analyst - Contact me if interested.
2.27.2008
Diebold Accidentally Leaks Results Of 2008 Election Early from John
HP Application Security Resource Library
2.25.2008
Invisible dots left by printers may breach EU privacy laws
If you have not yet read the paper posted on 2-21 "Lest We Remember: Cold Boot Attacks on Encryption Keys", at least check out this video.
cDc Releases Goolag - from Jamie
2.24.2008
Cisco confirms vulnerability in 7921 Wi-Fi IP phone
2.22.2008
Wiretapping GSM cellphones
2.21.2008
Lest We Remember: Cold Boot Attacks on Encryption Keys
Microsoft: Vista SP1 will break these programs
Design flaw in wireless VoIP handsets endanger the enterprise - Vendors skip verification of digital certificates "because of the processing overhead required"
2.20.2008
NTFS File System References [More]
Future of Japan's E-Voting in Doubt
2.19.2008
Saboteurs may have cut Mideast telecom cables: UN agency
In a completely unrelated story, where in the world is the USS Jimmy Carter?
2.18.2008
Shmoocon Notes: The Presentation by Sandy Clark (Mouse) on EVEREST (Evaluation and Validation of Election Related Equipment, Standards and Testing) was quite good. Unsurprisingly, the problems of E-Voting are as bad as ever.
Flawfinder is a program that examines source code and reports possible security weaknesses (``flaws'') sorted by risk level. - From Dale
Friendly 'worms' could spread software fixes - This is by no means new. Dave Aitel developed a framework for beneficial worms called Nematodes and HP researched beneficial worms in the early 00s (most evidence of which has disappeared). [Daily Dave]
2.14.2008
InsomniaShell is a tool for use during penetration tests, when you have ability to upload or create an arbitrary .aspx page. This .aspx page is an example of using native calls through pinvoke to provide either a reverse shell or a bind shell. It has the added advantage of searching through all accessible processes looking for a SYSTEM or Administrator token to use for impersonation.
2.13.2008
Airforce Cyber Command
2.12.2008
Adobe Reader and Acrobat JavaScript methods buffer overflow vulnerabilities - Adobe Reader EScript.api arbitrary code execution - Securing Your Web Browser
NIST 500-267 - A Profile for IPv6 in the U.S. Government
2.11.2008
NIST Budget Slashed
2.08.2008
New Authentication Scheme Proposed
2.06.2008
MayDay! Sneakier, More Powerful Botnet on the Loose - from John
Diebold voting machine key copied using a photo from their website!
2.05.2008
Google Blamed For Indexing Student Test Scores & Social Security Numbers
Carolinacon regional technology conference - Who needs an excuse to go to Chapel Hill?
2.04.2008
Cyber Security and Information Intelligence Research Workshop
2.03.2008
Universities fend off phishing attacks
2.02.2008
Who's Cutting the Cables?
2.01.2008
Italian Parliament To Mistakenly Legalize MP3 P2P [Original Italian]
DFRWS 2008 Forensics Challenge Overview
1.31.2008
MS08-001 Explained by Halvar Flake, et al.
1.30.2008
RIAA wants $1.5 million per CD copied
1.29.2008
The Société Générale Case - A Quest for Glory and a Bonus Ends in Disgrace
MS08-001 Exploit Video (Immunity Canvas)
1.28.2008
Uninformed Journal Vol 9
1.27.2008
(267) Warner sues "playable search engine," tests DMCA safe harbor
1.26.2008
Markets and Monkeys - Interview: Dr. Michael Shermer
1.25.2008
Fighting SPAM - AKA Mother, May I
EFF Action Alert - URGENT: Oppose Telecom Immunity and Tell Your Senator to Vote "No on Cloture"
1.23.2008
Firm Seeks Trainable Network Geek - Understands layers 1, 2, and 3. Can describe problems such as layer 2 loop scenarios and potential remedies. Understands where OSPF and BGP are used and why. Contact me for more information.
First case of "drive-by pharming" identified in the wild
1.22.2008
Going Against The Gradient - from Dave Aitel
CERT Secure Coding Standards
RIAA Website Wiped Clean by “Hackers” - from JCB
1.20.2008
OSSEC - Am Open Source, Multiplatform HIDS - from Michael
1.18.2008
CIA: Hackers to Blame for Power Outages - from the Dailydave
1.17.2008
Kernel-Level Remote TCP/IP and IGMP Vulnerabilities affect XP SP2, Vista, and Server 2003
MS08-001 (part 3) – The case of the IGMP network critical
North Dakota Man Charged for Spam Tracking / DNS Zone Transfer - from Ron
1.16.2008
NSA Backdoored Crypto AG Gear - Monitored Traffic for Years
Excel 0-Day
Fun with SSH - from Michael
FBI takes biometrics database proposal to U.K. - from John
1.15.2008
Flash attack could take over your router (UnPlug n Pray)
1.14.2008
US Policy Would Allow Government Access to Any Email
New Security Conference - SOURCE Boston 2008 - March 12-14
1.11.2008
Retrospective: 10 Security Blunders
The Sears "Community" Installation of ComScore - Sears admits to joining spyware biz - from Dan
1.10.2008
Wireless Power at CES from Chris
Steal This WiFi - by Bruce Schneier
Rootkit hides in MBR from John - GW: Every technique that's old is new again. What's next? Boot Sector Worms Propagating via Flash Drives?
Handy Diagram - How to Hack a Diebold E-Voting System
Diebold E-Voting Posters
1.09.2008
A former systems administrator at Medco Health Solutions Inc. was sentenced to 30 months in federal prison today for planting a logic bomb that could have taken down a corporate network that held customer health care information.
A proposed new RFID-enabled passport card intended for use by Americans frequently traveling to Canada, Mexico, Bermuda and the Caribbean poses serious security and privacy risks for users, the Center for Democracy and Technology (CDT) warned this week.
New iPhone Trojan Spreading from John [More]
Computer Science Education: Where Are the Software Engineers of Tomorrow?
1.07.2008
Island Hopping: The Infectious Allure of Vendor Swag
Roundup from Dark Reading:
Security's biggest train wrecks of 2007
The prank that could kill you
Evil Bits: Go-to sites for threat monitoring
Is Sears sending spyware to customers?
1.06.2008
FAA: Boeing's New 787 May Be Vulnerable to Hack Attack from Jacob
According to Cary Sherman of the RIAA, SONY BMG's in-house lawyer Jennifer Pariser "Misspoke" when testifying during Capitol v. Thomas trial
Capitol V Thomas was referenced in a previous NetSec post RIAA claims that ripping purchased CDs for personal use constitutes infringement - from Christopher
1.04.2008
One of our local agencies has an opening for a security / systems engineer. Drop me a line if you are interested.
New phishing technique: Fast Flux